Technologies Utilized
Below are the key technologies that were used to develop this tool:

YARA
A tool aimed at helping malware researchers and incident response teams to identify and classify malware samples.

Python
A high-level programming language used for developing the core functionality of the tool, including file analysis and report generation.

HTML5
The standard markup language used to create the structure of the webpages within the tool.

SciPy
A Python library used for scientific and technical computing, which supports numerical operations essential in malware analysis.

RE
Python’s regular expression library, used for searching and matching patterns within strings, essential for identifying patterns in binary data.
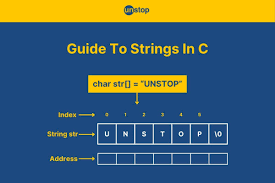
Strings
A Python module used to extract human-readable text from binary files, crucial for analyzing malware samples.

Base64
Used for encoding and decoding binary data into text, allowing the analysis of encoded malware samples.
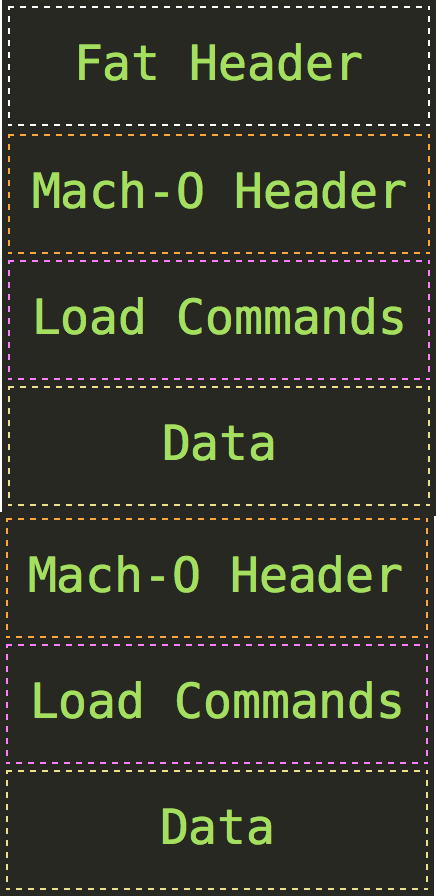
Macholib
A Python library used for handling Mach-O (Mac OS X) executable formats, which is useful for analyzing malware targeting macOS.
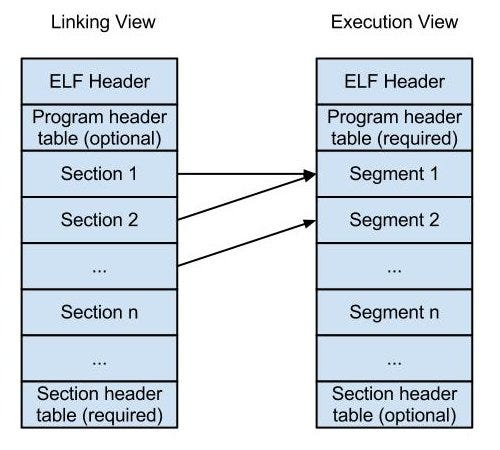
Pyelftools
A library for parsing and analyzing ELF (Executable and Linkable Format) files, which is essential for Linux malware analysis.
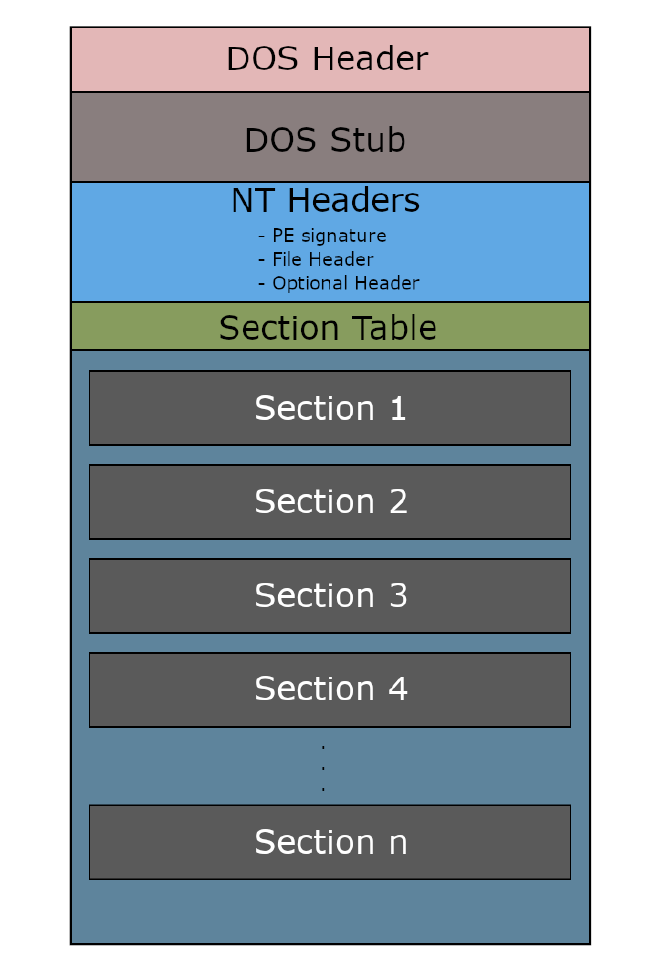
Pefile
A Python module used for parsing and analyzing PE (Portable Executable) files, typically found on Windows platforms.

SQLAlchemy
A SQL toolkit and Object-Relational Mapping (ORM) library for Python, used to manage databases storing malware reports and data.

CSS3
Used for styling and layout of the front-end, ensuring a responsive and visually appealing user interface across all devices.

NumPy
A library for numerical computations in Python, used for analyzing data extracted from malware samples.

Flask
A lightweight and powerful Python web framework used to develop the backend server that handles malware analysis, report generation, and user interaction.

Urllib
A library for working with URLs, used in downloading resources for analysis and retrieving data from the web.

VSCode
A lightweight code editor that was used for writing and debugging the source code of the project.

Bootstrap 5
A popular CSS framework that was used to quickly build responsive and modern user interfaces for the tool.
Hashlib
A Python module used for creating cryptographic hash functions like SHA-1, SHA-256, and MD5, which are useful for verifying malware file integrity and uniqueness.
GitHub Public
For more details, visit the project's GitHub repository, where the full code is available for download and contribution.
Visit GitHub Repository